Cyber Resilience for Wind Power Installations
Credit to Author: Contributed Content| Date: Wed, 01 Mar 2023 05:09:47 +0000

A tailored approach to evaluating and implementing benefit-based cybersecurity technologies for wind power plants.
Recent research and development (R&D) have provided insights into cybersecurity strategies and business cases for cybersecurity investments. These findings will help renewable sector entities tailor an approach to evaluating and implementing cybersecurity technologies for wind power plants.
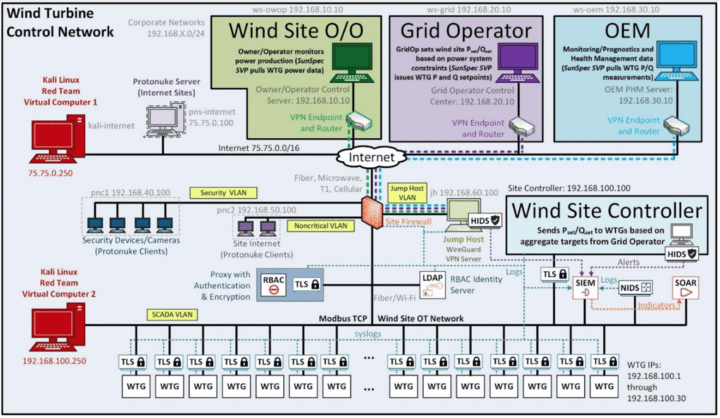
A Cyber Resilient Reference Architecture
The integration of secure technologies will underpin next-generation resilient designs for energy applications, informed by R&D, and implemented by industry. We used this survey to better understand R&D gaps, assess current state, and help the renewable industry improve informed architecture design. A security architecture includes several functional elements:
- Prevent. Block adversaries with access control, encryption, secure perimeters, and zero-trust architectures.
- Detect. Monitoring of network traffic and endpoint operations to recognize undesirable traffic.
- Analyze. Methods, including machine learning, to baseline normal behaviors and recognize abnormal.
- Decide/Visualize. Presentation of information to cyber defenders for quick recognition and response.
- Mitigate/Recover. Methods to stop a cyberattack and reverse any negative effects.
- Share. Securely providing indicators of compromise to support the defense of other organizations.
While there is no one-to-one mapping, security architecture functional elements are implemented using the following security tools:
- Prevent. Encryption, firewalls, data diodes, Identity and Access Management (IAM) tools.
- Detect and Analyze. Host/Network-based Intrusion Detection Systems (HIDSs/NIDSs) and Endpoint Detection and Response (EDR).
- Decide/Visualize. Security Information and Event Management (SIEM).
- Mitigate/Recover. Security Orchestration, Automation, and Response (SOAR).
- Share. Structured Threat Information eXpression (STIX), Trusted Automated eXchange of Intelligence Information (TAXII)
An example wind site architecture with these capabilities is shown in Figure 1.
Investing for Cyber Resilience
In support of a Department of Energy (DOE) Wind Energy Technologies Office (WETO) project, the teams at Idaho National Laboratory and Sandia National Laboratories built a high-fidelity implementation of wind turbine generators, site control systems, and communication architectures, which established the physical and cyber benefits to incorporating cybersecurity technologies in wind sites. The relative benefits versus cost for six technologies are provided in Figure 2 and include labor as full-time equivalents (FTEs). Costs and benefits are based upon polled large businesses unless otherwise noted.
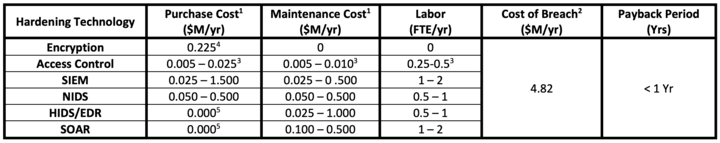
Notes:
1 Relative subscription and maintenance cost only for commercial tools.
2 Critical Infrastructure, Cost of a Data Breach Report, IBM Security, 2022.
3 Assuming an on-site LDAP (Lightweight Directory Access Protocol) or Active Directory Domain Controller for network access controls with regular maintenance and updates to the users, objects, and associated permissions. Control system devices may include access control features with network security services.
4 Point to point for 30 pairs. Some vendors offer integrated solutions.
5 No upfront software cost but there are maintenance/license costs.
Two representative remote and local cyberattacks were performed on wind sites with different cybersecurity technologies. In each test environment, a remote attack used compromised virtual private network credentials from a phishing attack to pivot through the wind network and change turbine setpoints, and a local attacker cut the lock on a tower and connected to the local network to issue turbine setpoints. Based on the attack sequences, cyber and physical resilience metrics were calculated for each test topology (Figure 3). Cyber resilience measured the ability to defend the system and recognize attacks earlier. Physical resilience measured the ability to maintain power generation despite attack. Encryption prevented the attacker from communicating directly with the turbines (Test 2), and the NIDS/HIDS recognized the attacks and provided defenders with SIEM alerts (Tests 3 and 4) or SOAR playbooks the data to execute a rapid response (Tests 5).
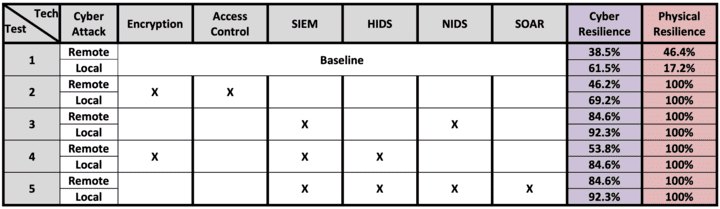
Cyber technologies reduce risks to wind asset owners and operators. Cyber risk in these experiments focused on the impact of two threat actors on a wind farm. By adding security technologies, attacks were successfully mitigated—demonstrating operational resilience and a return on investment (ROI) for integrating cybersecurity technologies within the renewable sector.
—Jake P. Gentle (jake.gentle@inl.gov) is a program manager and senior power systems engineer for Idaho National Laboratory (INL) and Jay Johnson (jjohns2@sandia.gov) is a distinguished member of Technical Staff at Sandia National Laboratories (SNL). Others who contributed to this article and research include: Michael McCarty is a senior cybersecurity researcher at INL; Craig Rieger, PhD, PE, who recently retired, was a chief control systems research engineer and a directorate fellow at INL; Rafer Cooley is a PhD student at the University of Wyoming CEDAR Lab and intern at INL; Brad Rothwell is a cybersecurity analyst at INL; Megan Culler is a power engineer and cybersecurity researcher at INL; and Brian Wright is a principal member of the Technical Staff at SNL.
The post Cyber Resilience for Wind Power Installations appeared first on POWER Magazine.